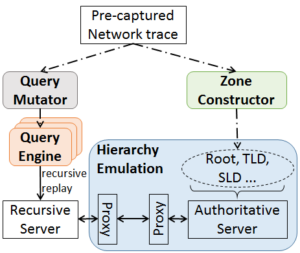
On August 25, 2017 Hurricane Harvey made landfall in south Texas, causing widespread property damage, displacing more than 30,000 people, and costing more than 45 lives (as of 2017-09-01).
We sympathize with those were hurt by this disaster, and hope for swift recovery for the region.
We recently examined the effects of Hurricane Harvey on the area using Trinocular, our internet outage detection system. Two key results:
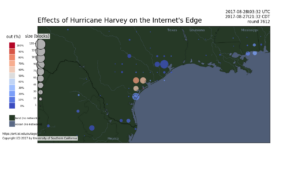
We see that landfall was followed by widespread Internet outages in the Corpus Christi area, with 40% or more home networks dropping off the Internet.
We see that over the following days, network outages grew in the Houston area, with many networks dropping off the Internet. However, the fraction of networks lost in Houston was much smaller than in the Corpus Christi area.
More details are on our Hurricane Harvey web page. We will update that page as we get more data in.
The dataset including Hurricane Harvey will be internet_outage_adaptive_a29all-20170702 and will be released in October 2017. Until the full data is released, we have a preliminary dataset through August 2017 available on request.